Don’t Fall For the New CryptoBlackmail Scam: Here’s How to Protect Yourself

Here’s how a CryptoBlackmail scam starts: A criminal contacts you over email or snail mail and insists they have evidence you cheated on your wife, there’s an assassin after you, or there’s a webcam video of you watching pornography.
To make the problem go away, the criminal asks for a few thousand dollars in Bitcoin or another cryptocurrency. But you should never respond or pay up. All the criminals have are empty threats, and they’re just trying to trick you.
What is CryptoBlackmail?
CryptoBlackmail is any sort of threat accompanied by a demand you pay money to a cryptocurrency address. Like traditional blackmail, it’s just a “pay up or we’ll do something bad to you” threat. The difference is that it demands payment in cryptocurrency.
Here are some examples of CryptoBlackmail:
- Physical mail saying “I know you cheated on your wife,” and demanding the equivalent of $2000 in Bitcoin sent to an included Bitcoin address.
- Emails saying “I’ve got an order to kill you,” followed by a demand to pay $2800 in Bitcoin to call off the assassination.
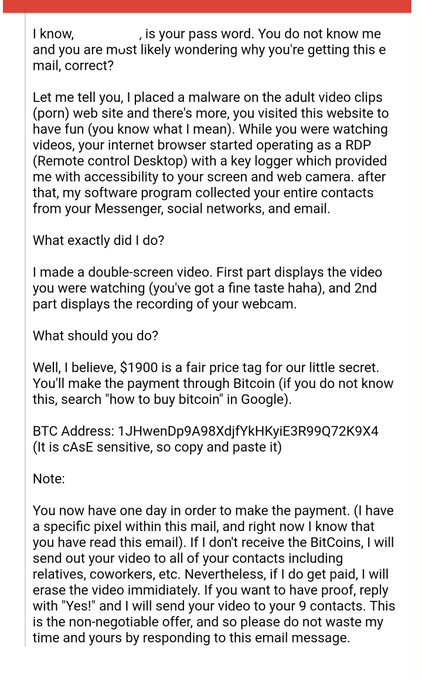
- Emails claiming an attacker has placed malware on your computer and recorded you watching pornography along with a video feed from your web camera. The attacker also claims to have copied your contacts, and threatens to send the video to them unless you pay $1900 in Bitcoin.
- Emails including a password to one of your online accounts along with a threat and a demand for $1200 to make the problem go away. The attacker just found your password in one of the many leaked password databases and hasn’t compromised your computer.
Bear in mind that the criminals almost certainly can’t follow through on their threat, and they probably doesn’t have the information they claim to have. For example, someone may just send letters saying “I know you cheated on your wife” to a large number of people, knowing that, statistically, many of them have. There almost certainly is not an assassin stalking you, either—especially an assassin who only works for a few thousand dollars! These are all empty threats, and there’s no reason to be scared of them.
Unfortunately, the scammers do trick some people. One scammer made about 2.5 BTC, or $15,500 USD, in the first two days of their scam on July 11 and 12. We know this because Bitcoin transaction records are public, so it’s possible to see how much money was sent to the scammer’s wallet address.
Don’t Negotiate or Pay. Don’t Even Respond.
Here’s the most important thing to know: This is not a personally targeted attack. The inclusion of one of your passwords from a breached database may make the threat seem personal, but it isn’t. They’ve just hoovered up your email address and password from a database. Criminals send large numbers of these emails (and even some physical letters,) hoping that just 1% of people will respond and pay up.
This is just like spam emails or tech support scammer phone calls. The criminals know most people won’t fall for their tricks, and they’ll quickly move on to find an easier mark if you aren’t falling for the scam.
Do not negotiate with the criminals, and definitely don’t pay anything. If you receive an email threat like this—especially if it’s an assassination threat!—you might want to report it to the police.
You should definitely report any threats sent as physical mail, too. It’s easier to catch criminals abusing the mail system than simply sending out emails. The US Postal Inspection Service doesn’t mess around.
Here’s an example of CryptoBlackmail:
Why Scammers Want Cryptocurrency
This type of scam has a lot in common with ransomware like CryptoLocker. Like ransomware, CryptoBlackmail makes a threat and demands payment to a cryptocurrency address. But, while ransomware actually holds your files hostage after compromising your computer, CryptoBlackmail is all empty threats.
CryptoBlackmail requests payment in cryptocurrency for the same reason ransomware does. It’s not possible to “undo” a transaction, and it’s hard for the authorities to track down the owner of a Bitcoin address. If the criminals requested you send money via a bank wire, that wire could be traced and the authorities could try to find the person who opened the bank account and maybe even get the money back. However, with cryptocurrency, the money is gone as soon as you send it.
While all the CryptoBlackmail scams we’ve seen demand you send Bitcoin to BTC (Bitcoin) wallet addresses, there’s nothing stopping criminals from requesting payment in “altcoins” like Monero.
How to Check if Your Passwords Have Leaked
You can check to see whether any of your passwords have been compromised using a service like Have I Been Pwned?. However, services like these don’t have every single password database that’s ever been stolen.
It’s best to just use a unique password everywhere so it doesn’t matter if one service suffers a breach. If you re-use the same password everywhere, your other accounts are vulnerable whenever one service leaks your password.
How to Protect Yourself
Here’s what you need to do to stay safe:
- Ignore the Scammers: First of all, forget the scam. As we said above, don’t try to negotiate with the scammer or pay them a single cent. All they have are empty threats. You will just be one of the vast majority of people contacted who aren’t paying up. We’ve never heard of a single case where a CryptoBlackmail scammer actually followed through on their threats.
- Don’t Re-Use Passwords: If a criminal sent you one of your passwords, it’s likely that password was from one of the many, many leaked password databases available online. You should never re-use passwords and, if you are re-using that leaked password on any other websites, you should change it right now. Use strong, unique passwords, especially for important accounts.
- Change Your Passwords: If you’re concerned a criminal might have your passwords, you should change them. If you’re using weak passwords or you’re re-using passwords on multiple websites, you should also change those. You need strong, unique passwords.
- Get a Password Manager: To help keep track of those unique passwords, we recommend you use a password manager like LastPass, 1Password, Dashlane, or even the password manager built into your web browser. They remember passwords for you, letting you use strong, unique passwords everywhere without having to remember them all.
- Enable Two-Factor Authentication: To further secure sensitive accounts like your email, social media, and financial accounts, we also recommend enabling two-factor authentication. You must enter a security code each time you sign in these accounts from a new device, and this code will be sent to your phone number via text message or generated in an app on your phone. This ensures that, even if a criminal has the password to your important accounts, they can’t get access to your secured accounts without the code.
- Secure Your Computer: To ensure a criminal isn’t actually spying on you or capturing sensitive data with a keylogger, be sure your computer is up-to-date with the latest security updates. You should also be using antivirus—Windows Defender is included on Windows 10. You may want to perform a scan with your preferred antivirus just to be sure there’s nothing nasty running in the background, too.
- Disable Your Webcam: If you’re really worried about someone spying on you with malware on your computer and capturing a webcam video, you can just disable your webcam when you aren’t using it. You don’t necessarily have to do this, and we don’t all do this here at How-To Geek—but heck, even Facebook-founder Mark Zuckerbergputs a piece of tape over his webcam.
The most important thing to do—aside from never paying the scammers—is to ensure you aren’t re-using passwords, especially if they’ve already leaked. Use strong, unique passwords and you won’t have to worry about password leaks. Just change a single password whenever there’s a leak—the service that suffered the password breach on will generally force you to change the password, anyway—and you’re done.
Image Source: Gualtiero Boff/Shutterstock.com
No comments:
Post a Comment