The Social Media Crime Fighters at FireEye Are Helping Facebook Find Fake Accounts
FireEye helped Facebook identify fake accounts with subversive international agendas. Here’s how.
Joe Pappalardo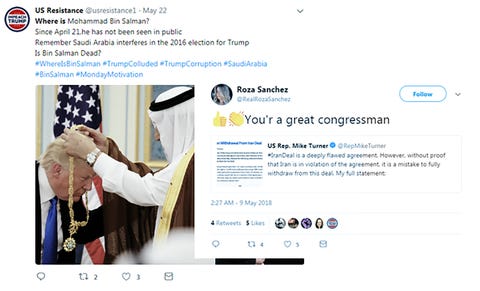
POPULAR MECHANICS
Above: These two accounts often tweet the same content. They were created the same month and are linked to Iranian phone numbers. “Roza’s” profile picture is from a hairstyle website.
Facebook, Google, and Twitter are waging an unseen but highly charged war on foreign hackers. Just as the Defense Department contracts private companies to build nuclear submarines, social media companies hire digital private eyes to find fake posts meant to influence the way Americans think about certain issues or candidates. One firm, FireEye, worked with Facebook to unearth fake pages during the summer buildup to this month’s midterm elections. The company reported a network of more than 650 fake accounts created in what was determined to be an Iranian government effort. Lee Foster, FireEye’s manager of information operations analysis, explains how they track down the offending accounts.
POPULAR MECHANICS: When you’re looking for foreign influence campaigns, where do you start?
LEE FOSTER: Forensic indicators. There’s the content-related side, where we’ll see something like internet accounts pretending to be Americans who are heavily promoting the Russian TV news channel RT or news agency Sputnik articles to U.S. audiences. There’s subversive activity there. Once, we observed social media personas masquerading as American liberals supportive of Senator Bernie Sanders heavily promoting Quds Day, a holiday established in Iran in 1979 to express support for Palestinians and opposition to Israel.
PM: How do you know those aren’t just Americans with an affection for Iranian holidays?
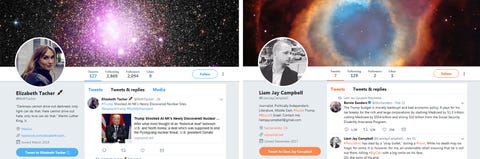
LF: There are other indicators, including registration history overlaps between inauthentic new sites and previous websites that originated in Iran and use the Persian language. Some sites share email registration histories. One, Liberty Front Press, had a registration email that appeared on advertisements for website designers based in Tehran. A number of the Twitter accounts we found affiliated with the inauthentic news sites were registered using Iranian phone numbers. None of these things on their own would be particularly conclusive, but when you bring them all together, you start to whittle down the list of possible alternative explanations.
POPULAR MECHANICS
PM: What kind of steps do information campaigns use to cover their tracks?
LF: Operators use VPNs [virtual private networks] to mask their true locations, even to the point where it makes it look like it’s coming from another country, in a way that some observers might try to blame that innocent third party as being responsible. These fake accounts appropriate some real person’s picture online. If you do a simple reverse image search, you’ll find the original account that owns it. Some hackers slightly alter the image so that when you do a reverse image search, it can’t pick up the original picture.
PM: Are there any signs of these campaigns slowing as they’re discovered?
LF: It’s not going away. This is a type of activity that is appealing to multiple actors. It has relatively low barriers to entry to successfully implement. We know how quickly the field of artificially generated videos, deep fakes, and voice mimicking is progressing. And we could start seeing operations that incorporate fake videos, or fake audio leaks, that sound or look just like a politician saying something.
No comments:
Post a Comment